In the ever-evolving landscape of technology, where data breaches and cyber threats have become commonplace, security testing has emerged as a critical component of any organization’s software development and deployment strategy. This article delves into the necessity of security testing, its evolution, and the fundamental principles that underpin it, such as password complexity, minimum password requirements, password validation, fuzz testing, privacy testing, and data access control.
The Imperative of Security Testing
As technology continues to advance, so do the tactics of malicious actors seeking to exploit vulnerabilities in software systems. The consequences of a security breach can be devastating, including financial losses, reputational damage, legal liabilities, and compromised customer trust. Therefore, companies today cannot afford to overlook the importance of security testing in their software development lifecycle.
The Evolution of Security Testing
Security testing has evolved significantly over the years, mirroring the advancements in technology and the sophistication of cyber threats. Originally, it consisted of manual code reviews and limited vulnerability scans. However, as organizations recognized the need for a more comprehensive approach, the field of security testing has expanded to encompass the following key elements:
- Password Complexity and Requirements
One of the foundational principles of security testing is ensuring that user authentication mechanisms are robust. Passwords are often the first line of defense against unauthorized access. Therefore, enforcing password complexity and minimum requirements (e.g., length, character diversity) is crucial. Advanced techniques like salting and hashing are employed to safeguard password storage.
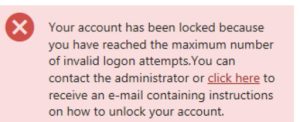
- Password Validation (3 Attempts and Blocked)
To thwart brute force attacks and protect against unauthorized access, it is essential to implement password validation mechanisms. These mechanisms typically involve limiting the number of login attempts and temporarily blocking access after a certain number of failed attempts. This measure is vital in deterring attackers from exploiting weak or stolen credentials.
- Fuzz Testing
Fuzz testing, also known as fuzzing, is a dynamic testing technique designed to uncover vulnerabilities in software by inputting unexpected, random, or malformed data. It is particularly effective in identifying weaknesses in application interfaces and data parsing functions. Fuzz testing helps organizations identify and rectify potential security flaws before attackers can exploit them.

- Privacy Testing
As concerns about data privacy and regulatory compliance grow, privacy testing has gained prominence. It involves assessing how user data is collected, stored, processed, and transmitted. This testing ensures that sensitive information is adequately protected and that applications adhere to data protection regulations, such as GDPR or HIPAA.
- Data Access Control
Controlling access to sensitive data is essential to prevent unauthorized users from viewing, modifying, or deleting critical information. Implementing role-based access control (RBAC), encryption, and robust authentication mechanisms are key aspects of data access control.

The Dynamic Landscape of Cybersecurity
The realm of cybersecurity is in a constant state of flux. Several factors drive the evolution of security testing and make it an essential practice:
- Evolving Threat Landscape
Cyber threats are becoming increasingly sophisticated, relentless, and adaptable. Attackers employ new tactics and exploit novel vulnerabilities with every passing day.
- Regulatory Frameworks
Data privacy regulations such as GDPR, HIPAA, and CCPA demand stringent security measures. Compliance necessitates robust security testing to ensure data protection and legal adherence.
- Reputation and Trust
A security breach not only leads to financial losses but can also irreparably damage an organization’s reputation. Security testing is essential for maintaining trust with customers, partners, and stakeholders.
- The Data Economy
In the digital age, data is a prized asset. Failing to protect data can result in significant financial and legal consequences.
Conclusion
In an era where data is a valuable currency and cyber threats are constantly evolving, security testing has become an indispensable part of software development and deployment. The evolution of security testing methodologies reflects the need for organizations to adapt to an ever-changing threat landscape.
By embracing fundamental security principles such as password complexity, minimum requirements, password validation, fuzz testing, privacy testing, and data access control, companies can fortify their applications against vulnerabilities, reduce the risk of data breaches, and safeguard their reputation and customer trust. In an age where security breaches can have catastrophic consequences, proactive security testing is not just a best practice; it’s a business imperative.
The International Software Testing Qualifications Board (ISTQB) addresses various aspects of software testing, including security testing, process, and design considerations.
- Security Testing: ISTQB recognizes the critical importance of security in software applications. Security testing focuses on identifying vulnerabilities, weaknesses, and potential threats within the software. This encompasses evaluating how well the software can withstand external attacks, secure data, and protect against breaches. ISTQB provides guidelines and best practices for security testing to ensure that testers can assess the software’s resilience against cyber threats effectively.
- Process: ISTQB emphasizes the need for standardized testing processes. It offers guidance on creating, implementing, and optimizing testing processes within software development lifecycles. This includes aspects like test planning, test case development, execution, and reporting. Following standardized processes helps ensure consistency and reliability in software testing, resulting in higher-quality software products.
- Design: In software testing, design considerations are crucial for creating effective test cases. ISTQB provides principles and techniques for designing test cases that cover various aspects of software functionality, usability, performance, and more. Test case design ensures that the software is thoroughly and systematically tested, helping to detect and report defects more efficiently.
By addressing these elements—security testing, testing processes, and design—ISTQB contributes to the development of robust and high-quality software systems while enabling testers and quality assurance professionals to follow standardized best practices throughout the software testing life cycle.
We offer comprehensive security testing services, along with complimentary consultations. Our team consists of highly skilled consultants certified by ISTQB and NIST, with extensive experience collaborating with cybersecurity and intelligence agencies. Feel free to visit our website qabound.com and get in touch to schedule an appointment today.
Reference:
- https://www.getsoftwareservice.com/different-test-types/
- https://www.gasq.org/files/content/gasq/downloads/certification/ISTQB/Advanced%20Level/Advanced_Security_Tester_Syllabus_-_GA_2016.pdf
- https://qabound.com/testing-strategy/
- https://www.linkedin.com/pulse/istqb-foundation-level-quick-guide-shady-ahmed-mohamed/
- https://www.utcluj.ro/media/page_document/78/Foundations%20of%20software%20testing%20-%20ISTQB%20Certification.pdf



1 comment
I would ensure other basic things such as rate limiting are covered. I understand you’re showing the bare minimum though. It’s absolutely scandalous how many companies don’t have these basic protective measures. I really believe it should become legislation and not just some fancy ISO to seem a bit better.
Comments are closed.