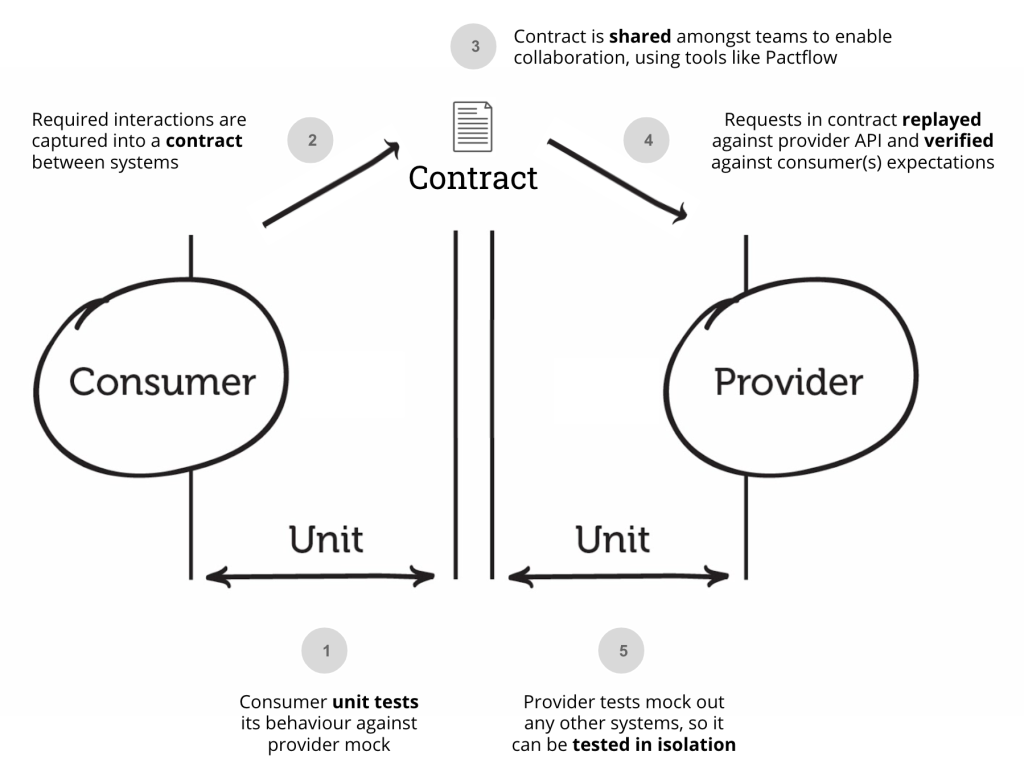
If you are new to the concept of contract testing or looking...
Read More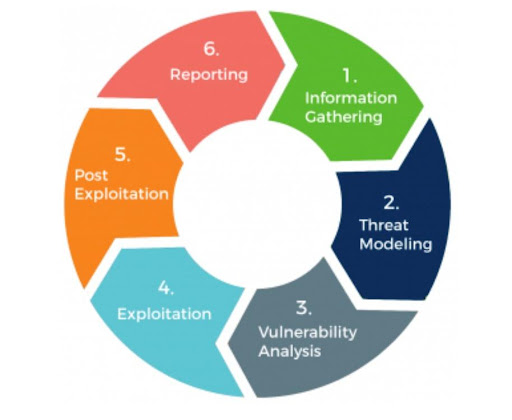
In the ever-evolving landscape of technology, where data breaches and cyber threats have become commonplace, security testing has emerged as a critical component of any organization's software development and deployment strategy. This article delves into the necessity of security testing, its evolution, and the fundamental principles that underpin it, such as password complexity, minimum password requirements, password validation, fuzz testing, privacy testing, and data access control.
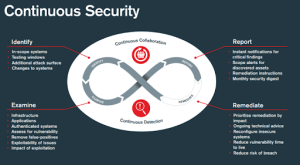
 The Imperative of Security Testing
As technology continues to advance, so do the tactics of malicious actors seeking to exploit vulnerabilities in software systems. The consequences of a security breach can be devastating, including financial losses, reputational damage, legal liabilities, and compromised customer trust. Therefore, companies today cannot afford to overlook the importance of security testing in their software development lifecycle.
The Imperative of Security Testing
As technology continues to advance, so do the tactics of malicious actors seeking to exploit vulnerabilities in software systems. The consequences of a security breach can be devastating, including financial losses, reputational damage, legal liabilities, and compromised customer trust. Therefore, companies today cannot afford to overlook the importance of security testing in their software development lifecycle.
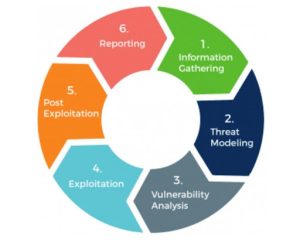
 The Evolution of Security Testing
Security testing has evolved significantly over the years, mirroring the advancements in technology and the sophistication of cyber threats. Originally, it consisted of manual code reviews and limited vulnerability scans. However, as organizations recognized the need for a more comprehensive approach, the field of security testing has expanded to encompass the following key elements:
The Evolution of Security Testing
Security testing has evolved significantly over the years, mirroring the advancements in technology and the sophistication of cyber threats. Originally, it consisted of manual code reviews and limited vulnerability scans. However, as organizations recognized the need for a more comprehensive approach, the field of security testing has expanded to encompass the following key elements:
- Password Complexity and Requirements
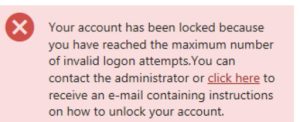
- Password Validation (3 Attempts and Blocked)
- Fuzz Testing

- Privacy Testing
- Data Access Control
 The Dynamic Landscape of Cybersecurity
The realm of cybersecurity is in a constant state of flux. Several factors drive the evolution of security testing and make it an essential practice:
The Dynamic Landscape of Cybersecurity
The realm of cybersecurity is in a constant state of flux. Several factors drive the evolution of security testing and make it an essential practice:
- Evolving Threat Landscape
- Regulatory Frameworks
- Reputation and Trust
- The Data Economy
- Security Testing: ISTQB recognizes the critical importance of security in software applications. Security testing focuses on identifying vulnerabilities, weaknesses, and potential threats within the software. This encompasses evaluating how well the software can withstand external attacks, secure data, and protect against breaches. ISTQB provides guidelines and best practices for security testing to ensure that testers can assess the software's resilience against cyber threats effectively.
- Process: ISTQB emphasizes the need for standardized testing processes. It offers guidance on creating, implementing, and optimizing testing processes within software development lifecycles. This includes aspects like test planning, test case development, execution, and reporting. Following standardized processes helps ensure consistency and reliability in software testing, resulting in higher-quality software products.
- Design: In software testing, design considerations are crucial for creating effective test cases. ISTQB provides principles and techniques for designing test cases that cover various aspects of software functionality, usability, performance, and more. Test case design ensures that the software is thoroughly and systematically tested, helping to detect and report defects more efficiently.

